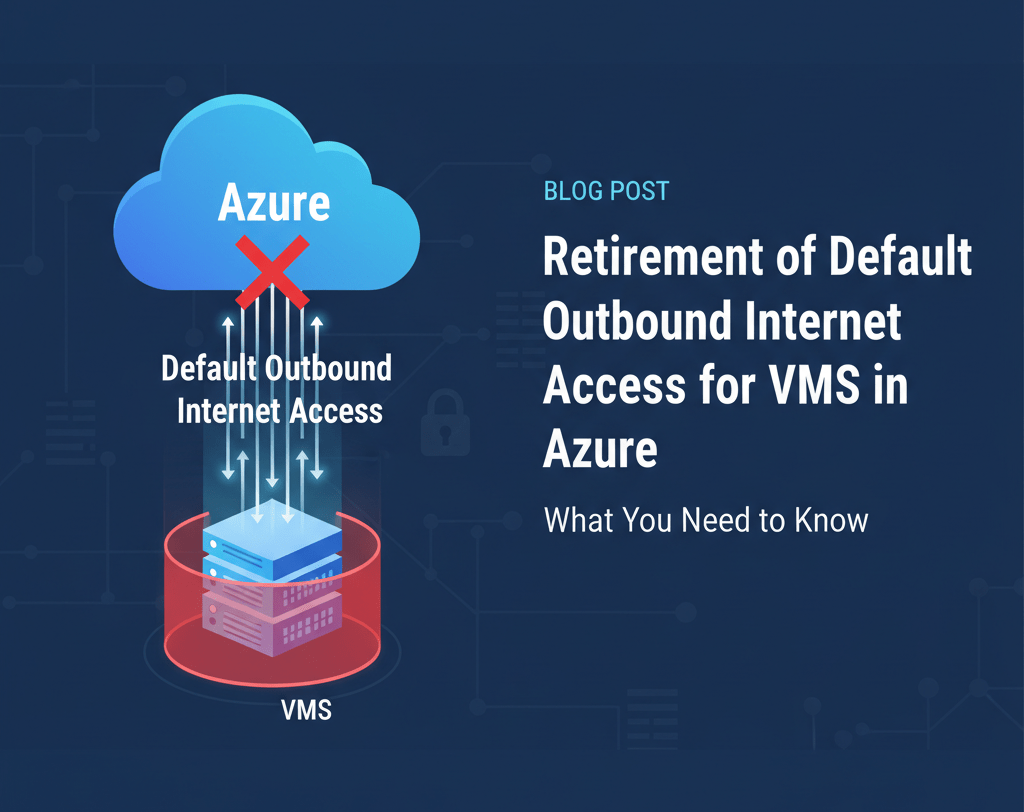
Microsoft is set to retire default outbound internet access for Azure Virtual Machines (VMs) on September 30, 2025. This change will impact how new Azure VMs connect to the internet, signaling a major shift toward enhanced security and network control for all Azure customers worldwide.
What Is Default Outbound Internet Access?
Default outbound internet access is a feature where Azure VMs, without an explicitly defined outbound method, automatically receive internet connectivity via a default public IP address assigned by Azure. This simplifies deployment but comes with security and operational limitations.
Why Is Microsoft Retiring Default Outbound Internet Access?
Moving to a secure-by-default model is at the heart of this decision. Microsoft wants customers to make explicit outbound connectivity choices, providing better control, traceable IP resources, and increased alignment with corporate security and compliance requirements.
Key Reasons:
- Enhanced Network Security
- Greater Control over Public IPs
- Improved Compliance and Troubleshooting Capabilities
Who Is Affected by the Change?
- New Virtual Machines: From September 30, 2025, VMs deployed in Azure will not have internet access unless an explicit outbound connectivity method is configured.
- Existing VMs: Virtual machines created before this date will continue to use default outbound internet access, but Microsoft strongly advises transitioning to explicit methods for reliability and security.
- Not Affected: Azure Cloud Services (extended support) users are not impacted by this change.
What Are the Alternatives to Default Outbound Access?
Explicit Outbound Connectivity Methods:
- Azure NAT Gateway: Centralizes outbound connectivity and uses static public IPs.
- Azure Load Balancer (Outbound Rules): Configures outbound rules to manage internet access for VMs.
- Directly Attached Public IP Address: Assigns a dedicated public IP to the VM’s network interface.
- Virtual Appliances or Azure Firewall: For advanced scenarios demanding robust security and traffic management.
Steps for a Smooth Transition
- Audit Existing Deployments: Use Azure Advisor to identify VMs still using default outbound access.
- Select the Right Outbound Method: Consider security needs, compliance, and scale.
- Implement Explicit Connectivity: Configure NAT Gateway, outbound rules, or attach public IPs as needed.
- Test and Validate: Ensure outbound access works for all critical workloads and services
Benefits of Explicit Outbound Connectivity
- Enhanced Security: Eliminates unintended public internet exposure.
- Consistent IP Usage: Simplifies whitelisting and troubleshooting.
- Regulatory Compliance: Meets tighter security mandates and audit requirements.
Conclusion
With the retirement of default outbound internet access, Azure customers must plan and transition to explicit outbound connectivity methods. This proactive step will align Azure environments with modern cloud security best practices, offering more control and reducing risks.
FAQs
- When is default outbound internet access for Azure VMs retired?
September 30, 2025. From this date, new VMs will not have internet connectivity unless explicitly configured. - Do existing VMs lose internet access after this date?
No, existing VMs will retain default outbound access. However, moving to explicit methods is strongly recommended. - Which outbound connectivity options can be used?
- Azure NAT Gateway
- Azure Load Balancer outbound rules
- Direct Public IP assignment
- Azure Firewall or virtual appliances
- How can affected VMs be identified?
Use Azure Advisor’s recommendations under the “Operational Excellence” section to spot VMs with default outbound access.





Leave a Reply