As organizations increasingly rely on cloud infrastructure to power their applications and services, it’s more important than ever to ensure that your Amazon Web Services (AWS) environment is secure. Securing AWS infrastructure is essential to ensure the confidentiality, integrity, and availability of your applications and data. In this blog post, we’ll go over some best practices for securing AWS infrastructure, including how to implement the least privilege, how to use IAM policies, and how to set up network security.
- Use Identity and Access Management (IAM) policies to control access to your AWS resources. IAM allows you to create users, groups, and roles, and assign permissions to them using policies. This enables you to grant the minimum necessary permissions to each user, group, or role, reducing the risk of accidental or malicious access to your resources.
IAM policies are an essential tool for implementing the least privilege in AWS. These policies allow you to specify exactly what actions users or resources can take and on which resources they can take them. For example, you can use IAM policies to allow a user to only read objects in a specific S3 bucket, or to only start and stop EC2 instances in a particular VPC. You can also use IAM policies to grant or deny access to specific API actions, such as the ability to create or delete IAM users. - Enable Multi-Factor Authentication (MFA) for all IAM users. MFA requires users to provide an additional authentication factor, such as a one-time code from a physical or virtual MFA device, in addition to their username and password. This significantly increases the security of your AWS account and helps prevent unauthorized access.
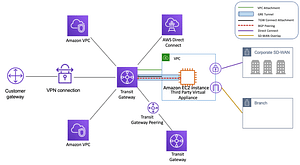
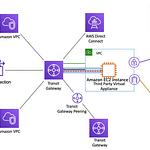
- Another important aspect of securing your AWS infrastructure is properly configuring network security. This includes setting up VPCs, subnets, and security groups to control inbound and outbound traffic to your resources. It’s important to only allow traffic that is necessary for your applications and services and to block all other traffic. For example, if you have an EC2 instance that only needs to be accessed via SSH from a specific IP range, you should configure your security group to only allow incoming SSH traffic from that range.
Use Amazon Virtual Private Cloud (VPC) to isolate your resources within a virtual network. VPC enables you to control the visibility of your resources and control inbound and outbound traffic using security groups and network access control lists (ACLs). This helps you protect your resources from unauthorized access and external threats. - Enable AWS Shield to protect your resources from distributed denial of service (DDoS) attacks. AWS Shield is a managed DDoS protection service that automatically detects and mitigates DDoS attacks, helping you ensure the availability of your applications.
- Use AWS Config to monitor and audit the configuration of your AWS resources. AWS Config enables you to track changes to your resources and their configurations, as well as assess the compliance of your resources with predefined rules. This helps you detect and prevent unauthorized changes to your resources and maintain compliance with security and regulatory standards.
- Enable AWS CloudTrail to track and log API calls to your AWS account. AWS CloudTrail enables you to track changes to your resources and their configurations, as well as identify patterns of suspicious activity. This helps you detect and respond to security threats and comply with auditing and regulatory requirements.
- Use Amazon Inspector to assess the security and compliance of your Amazon Elastic Compute Cloud (EC2) instances. Amazon Inspector is a security assessment service that analyzes your EC2 instances for vulnerabilities and misconfigurations and provides recommendations for remediation. This helps you ensure the security of your instances and maintain compliance with security and regulatory standards.
- Use AWS Key Management Service (KMS) to securely manage and store your encryption keys. KMS enables you to create and manage your own encryption keys, as well as use predefined keys for encryption and decryption. This helps you secure your data at rest and in transit, and comply with data protection and regulatory requirements.
- Use Amazon S3 bucket policies and access control lists (ACLs) to control access to your Amazon Simple Storage Service (S3) buckets and objects. S3 bucket policies and ACLs enable you to specify who can access your S3 buckets and objects, as well as what actions they can perform. This helps you secure your data and ensure that it is only accessed by authorized users.
- Use Amazon CloudWatch to monitor and alert on security events. CloudWatch enables you to set up alarms and notifications based on specific security events, such as access-denied errors or failed authentication attempts. This helps you detect and respond to security threats in real-time.
In conclusion, following these best practices can help you secure AWS infrastructure and protect your applications and data from unauthorized access and external threats.
By following these best practices, you can significantly improve the security of your AWS infrastructure and protect your applications and data. However, it’s important to remember that security is an ongoing process, and you should regularly review and update your security measures to ensure that they are effective. You can also check the official AWS blog on securing infrastructure