Customer managed KMS in IAM Identity Center Best Practices
Introduction Managing encryption keys is a core part of cloud security and compliance. This article…
Customer managed KMS in IAM Identity Center Best Practices
IntroductionThe shift to centralized identity with IAM Identity Center raises new encryption considerations. Using customer…
AWS Security, customer managed KMS in IAM Identity Center
Introductioncustomer managed KMS in IAM Identity Center is an essential control for organizations that need…
Generative AI Infrastructure on AWS, Azure, GCP
Introduction The GenAI Gold Rush demands robust, scalable Generative AI infrastructure to train and serve…
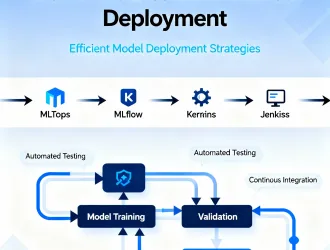
MLOps Tools and Best Practices for Streamlined Deployment
IntroductionMLOps tools and best practices are essential to move models from notebooks to reliable production…
Implementing Zero Trust Architecture in Hybrid Cloud
Introduction Implementing Zero Trust Architecture in Hybrid Cloud demands a shift from perimeter-centric security to…
Generative AI and Amazon Bedrock for Rapid Apps
IntroductionThe rise of generative AI and Amazon Bedrock is reshaping how teams prototype and ship…
Amazon EC2 M4 Mac instances for iOS and macOS
IntroductionThe Amazon EC2 M4 Mac instances bring new capacity and performance options for iOS and…
Deploying a Serverless Web App with AWS Lambda and DynamoDB
IntroductionBuilding a serverless web app can dramatically reduce operational overhead while improving scalability. This guide…
Migrating existing applications to AWS and Modernizing
Migrating existing applications to AWS Introduction Migrating existing applications to AWS is a strategic move…