Imagine working for an enterprise having 50-plus AWS accounts. AWS has 22 regions as of writing this post. If you have resources deployed across 50 plus AWS accounts and 22 regions; that brings around 1100 instances to work with. Hard to imagine right?
What if I tell you that you can manage resources across multiple accounts and regions using AWS lambda and boto3? I have personally used this setup to Update the Cloudwatch Log retention period across accounts, Get unattached volumes, Delete EBS and RDS snapshots greater than X days, and Weekly EC2 and RDS report. You can basically manage AWS resources centrally across accounts and do anything with this hierarchy
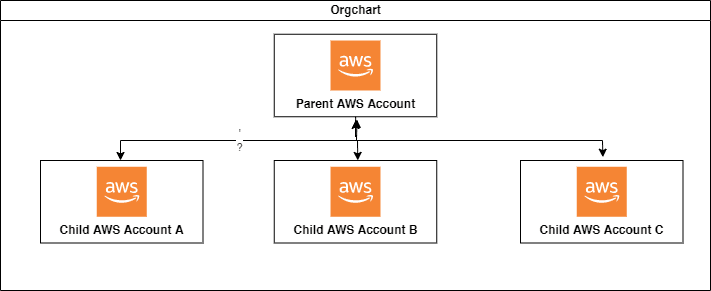
A high-level diagram of the setup
We will be considering an AWS account which we’ll refer to as a “Parent AWS Account”, similarly we’ll have other AWS accounts acting as Child. Refer to the diagram below for a better understanding
Things we would be using to achieve this:
- IAM – Roles
- Lambda – Written in Python using boto3
Configuring cross-account IAM Roles
To manage AWS resources across multiple accounts, the lambda function will need to assume a role in the target account using the AWS Security Token Service (STS). This can be done by calling the assume_role method of the boto3 STS client and specifying the target account and role.
To create an IAM role for the above setup, follow these steps:
- Sign in to the AWS Management Console and navigate to the IAM service.
- In the left-hand navigation menu, click on “Roles” and then click the “Create role” button.
- In the “Choose the service that will use this role” section, select “Lambda” from the list of options.
- In the “Permissions” section, select the permissions that the role should have. These should include permissions for the AWS resources that the lambda function will need to access and manipulate.
- Give the role a name and optional description, then click the “Create role” button.
Once the role has been created, you will need to attach it to the lambda function that will be accessing and manipulating the AWS resources. This can be done by specifying the role’s ARN (Amazon Resource Name) in the lambda function’s configuration.
It is also a good idea to assign the IAM policy “AWSLambdaExecute” to the role, as this will allow the lambda function to assume the role and access the targeted resources.
By creating and attaching an IAM role to the lambda function, you can ensure that the function has the necessary permissions to access and manipulate the targeted AWS resources across multiple accounts and regions.
Setup Lambda that can manage resources across accounts
Here is an example of a lambda function that can be used to manage AWS resources across multiple accounts and regions using boto3:
import boto3
def lambda_handler(event, context):
# Assume role in target account
sts_client = boto3.client('sts')
assumed_role_object = sts_client.assume_role(
RoleArn='arn:aws:iam::<TARGET_ACCOUNT_ID>:role/<TARGET_ROLE_NAME>',
RoleSessionName='<ROLE_SESSION_NAME>'
)
# Use temporary credentials to access resources in target account
temp_credentials = assumed_role_object['Credentials']
boto3.setup_default_session(
aws_access_key_id=temp_credentials['AccessKeyId'],
aws_secret_access_key=temp_credentials['SecretAccessKey'],
aws_session_token=temp_credentials['SessionToken']
)
# Set default region for all boto3 clients and resources
boto3.Session().set_config_variable('region_name', '<REGION_NAME>')
# Create EC2 instance in target region
ec2_client = boto3.client('ec2')
ec2_client.run_instances(
ImageId='ami-<AMI_ID>',
InstanceType='t2.micro',
MinCount=1,
MaxCount=1
)
# Delete S3 bucket in target region
s3_client = boto3.client('s3')
s3_client.delete_bucket(Bucket='<BUCKET_NAME>')In this example, the lambda function first assumes a role in the target account using the boto3 STS client. It then uses the temporary credentials from the assumed role to access and manipulate resources in the target account and region.
The function then sets the default region for all boto3 clients and resources to the specified region and uses the boto3 EC2 and S3 clients to create an EC2 instance and delete an S3 bucket in that region.
This is just a basic example of how boto3 and lambda can be used to manage AWS resources across multiple accounts and regions. More complex functionality can be implemented by adding additional logic and boto3 client calls to the function.